RIFT: F5 CVE-2020-5902 and Citrix CVE-2020-8193, CVE-2020-8195 and CVE-2020-8196 honeypot data release
tl;dr
NCC Group is today releasing three months of honeypot web traffic data related to the F5 CVE-2020-5902 and Citrix CVE-2020-8193, CVE-2020-8195 and CVE-2020-8196 exploitation events from earlier in 2020. Our objective is to enable all threat intelligence researchers to gain further understanding and contribute back to the community.
About the Research and Intelligence Fusion Team (RIFT):
RIFT leverages our strategic analysis, data science, and threat hunting capabilities to create actionable threat intelligence, ranging from IOCs and detection capabilities to strategic reports on tomorrow’s threat landscape. Cyber security is an arms race where both attackers and defenders continually update and improve their tools and ways of working. To ensure that our managed services remain effective against the latest threats, NCC Group operates a Global Fusion Center with Fox-IT at its core. This multidisciplinary team converts our leading cyber threat intelligence into powerful detection strategies.
Headlines
What?
RIFT are releasing 3 months worth of honeypot web traffic data showing attack and exploitation of F5 Big-IP and a small amount of Citrix ADC exploitation. All the findings in this post come from this data, with the exception of one webshell we've uploaded to VirusTotal.
Note: some of the analysis in this post is based on second order artifacts. What is in the PCAP are payload URLs for the RATs but not binaries themselves.
Why?
This represents a significant amount of data that highlights just how widely exploited the issues were.
We believe that by open sourcing this data it will allow other threat intelligence organisations in academia as well as the public and private sectors to corroborate their findings to help further attribute attacks as well as identify and highlight attacker-tactics.
This large corpus of malicious traffic can be used for a variety of tactical activities including:
- developing and testing signature & behavioral detection
- highlighting common back doors facilitating discovery of known implants
When?
We established our first F5 honeypot on July 3rd, 2020.
Public exploits were released July 5th, 2020.
We observed exploitation by UNC757 / Pioneer Kitten (Iran) on July 6th, 2020
https://us-cert.cisa.gov/ncas/analysis-reports/ar20-259a / 4a1fc30ffeee48f213e256fa7bff77d8abd8acd81e3b2eb3b9c40bd3e2b04756.
This is new intelligence as the original FBI reporting does not highlight just how quickly this vulnerability was weaponized and utilized by APT actors. It is not in the PCAP but the CVS data we are also making available.
We established network level logging on July 7th, 2020
So?
The PCAP of network traffic highlights huge uptick in attacks from July 7th, 2020 onwards, with hundreds of attacks per day.
Interesting insights from the data
There are various insights in this dataset, we've summarized a few of our observations below.
Volumes

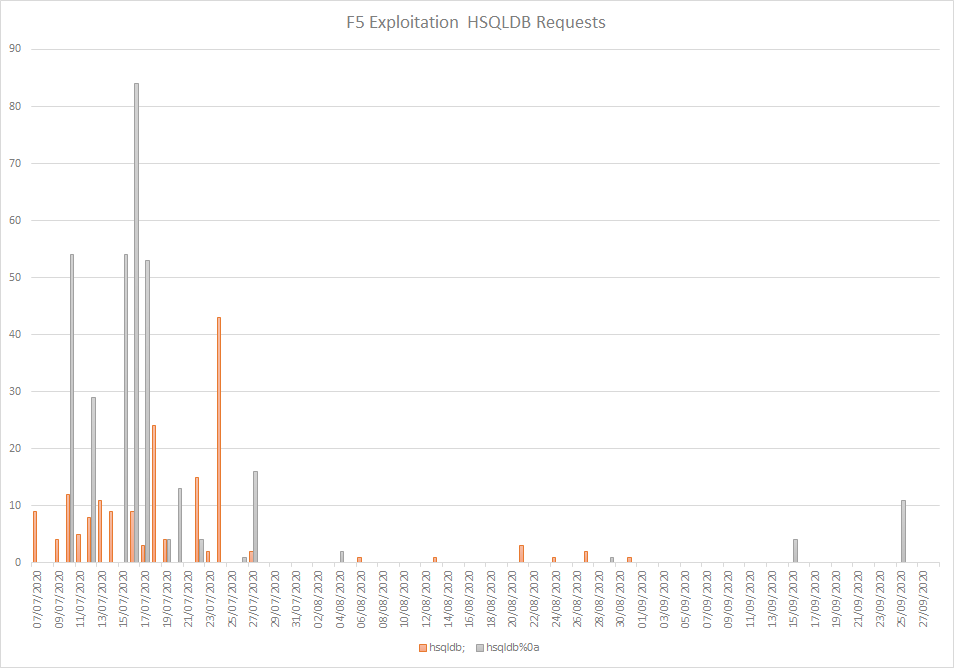
Attacker Techniques, Tactics and Procedures
We observed that attackers deploy a range of access/persistence techniques. The most common can be summarized as:
- Deployment of web shells - typically APT
- Adding of backdoor user accounts - typically APT
- Adding backdoor SSH key for persistent access
- Deployment of reverse shells (TCP/HTTP, netcat etc.)
- Deployment of Remote Access Toolkits (RATs) - we observed various RATs including PupyRAT and GoMet
- Backdooring of system files (e.g. Linux binaries)
- Password dumping
We also saw a common set of initial actions, again across a spectrum, including:
- Information gathering collecting various files from the filesystem and uploading to a remote server
- Deployment of coin miners
- Deployment of botnet loaders, e.g. Mirai derivatives
Backdoor accounts we've attributed to APT activity
These are the backdoor user accounts we observed, many of which we believe can attributed to APT activity specifically:
- snmpd
- systems
- f5admin
- f5_localuser
- f5_remoteuser
- root
- supporter
- test0
Exploitation and persistence agility and innovation insights
Beyond the insights above we also made a number of observations from the data around threat actor capability and their ability to innovate.
These insights include:
- Alternative execution methods
- REST execution which used a backdoor account
- Mitigation bypasses observed being exploited in the wild before it was reported
- See the 'Mitigation Bypass' sections in our original blog
- Adoption trends for both the hsqldb and mitigation bypass techniques can be found in the data.
- We discovered a JSP shell which modifies the existing welcome.jsp page, and cannot be detected passively
- It looks just like the normal welcome.jsp page
- When you supply the "cj" header, it executes the supplied command.
- IOC:
- 996258ac921c4e1e1d641cb5614fe5e6c19d01ba - which we've uploaded to VirusTotal
- /usr/local/www/tmui/WEB-INF/classes/org/apache/jsp/tmui/login/welcome_jsp.class
- Password spraying
- The data shows attackers password spraying the Citrix Nitro API with common default passwords, which facilitate Remote Code Execution if successful.
- We saw the following accounts being sprayed against Citrix:
- nsroot:nsroot
- root:Unidesk1
- administrator:Unidesk1
- root:v9Yx*6uj
- Password spraying for backdoor accounts
- The data also shows password spraying for backdoor accounts,
- bigipuser3 (a known backdoor account).
- This could be the original attacker not keeping track of hosts they've compromised or could be a secondary attacker looking to utilize another's access.
- The data also shows password spraying for backdoor accounts,
- Scanning for webshells
- We data shows extensive scanning for common webshells - this could be benign Threat Intelligence gathering, or could again be the original attacker or secondary attacker looking to make use
- Cloud awareness - going after AWS IAM credentials via the metadata URL
Call to action - if you didn't patch then hunt
The data shows that if organisations did not patch the F5 vulnerability in a timely fashion - that is not mitigate, but patch per our original blog - then a variety of threat actors could have access to the affected devices.
Therefore NCC Group are again highlighting that patching late or mitigating only in the case of the F5 vulnerability was not enough and organisations should inspect their devices for signs of compromise based on the information in our original blogs and that contained here.
Network Signatures For F5 Big-IP TMUI hsqldb
alert http any any -> $HOME_NET any (msg:"RIFT - Exploit - F5 Big-IP TMUI hsqldb request bypass 1"; flow:established,to_server; content:"/hsqldb|3b|"; depth:8; http_uri; fast_pattern; reference:cve,2020-5902; reference:url,www.criticalstart.com/f5-big-ip-remote-code-execution-exploit/; reference:url,support.f5.com/csp/article/K52145254; classtype:attempted-admin; sid:1; rev:1;)
alert http any any -> $HOME_NET any (msg:"RIFT - Exploit - F5 Big-IP TMUI hsqldb request bypass 2"; flow:established,to_server; content:"/hsqldb%"; depth:8; http_raw_uri; fast_pattern; reference:cve,2020-5902; reference:url,www.criticalstart.com/f5-big-ip-remote-code-execution-exploit/; reference:url,support.f5.com/csp/article/K52145254; classtype:attempted-admin; sid:2; rev:1;)
Data
The data is on GitHub - https://github.com/nccgroup/Cyber-Defence/tree/master/Intelligence/Honeypot-Data/2020-F5-and-Citrix